
Cybersecurity Awareness Month: Spotlight on ICS/OT Security
Believe it or not, Industrial Control Systems and Operational Technology (ICS/OT), the lifelines of our critical infrastructure, are seeing rising threats. Last year, more than
Home / Blog / Industrial Cybersecurity / A Guide to OT Security Components Based on the NIST Cybersecurity Framework
Operational Technology (OT) systems, such as industrial control systems (ICS) and Supervisory Control and Data Acquisition Systems (SCADA), are critical components of modern infrastructure, powering essential services such as power generation, transportation, and manufacturing making them attractive targets for cybercriminals seeking to cause disruption or steal sensitive data.
Additionally, many OT systems were not designed with cybersecurity in mind and may lack the necessary security controls to protect against modern threats. This presents a significant challenge for organizations as they work to secure their critical infrastructure and prevent disruptive or damaging cyberattacks. It is essential for organizations to take proactive measures to ensure their OT systems and protect against potential threats.
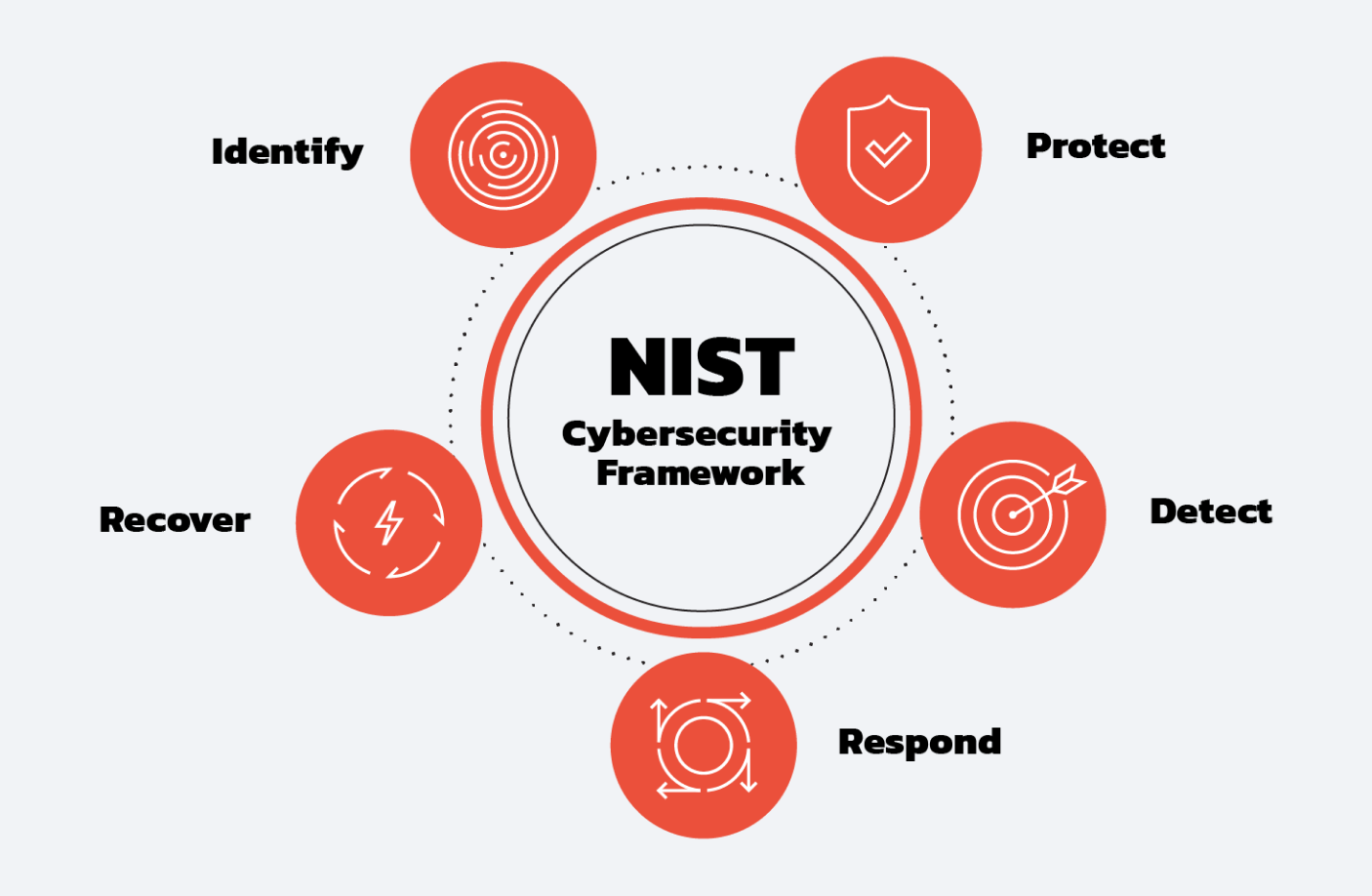
The NIST Cybersecurity Framework provides a comprehensive approach to managing and reducing cybersecurity risk. The framework provides a common language and structure for organizations to understand and manage cybersecurity risk and can be applied to OT systems. This blog post will provide a guide to the components of the NIST Cybersecurity Framework relevant to OT security, including:
This component involves identifying the assets, systems, and processes that are critical to the organization’s operations and require protection. This also involves understanding the potential threats and risks to these assets. Knowing the precise location and configuration of assets, such as control systems, devices, and networks, is the first step in protecting them from cyberattacks. Accurate inventory management ensures that all assets are properly secured, patched, and updated, reducing the risk of vulnerabilities that attackers could exploit.
This component involves implementing security controls and strategies to protect the organization’s critical assets from cyber threats. This includes implementing access controls, encryption, firewalls, and other security technologies. For example, in an ICS, security controls may consist of network segmentation, software updates, and antivirus software.
This component involves implementing monitoring and detection systems to identify and respond to potential security incidents. This includes logging, intrusion detection systems, and security information and event management (SIEM) systems. For example, in an ICS, detection systems may consist of network monitoring, event logging, and intrusion detection systems. Logging helps organizations maintain a record of events, changes, and anomalies that occur within their OT environment, providing valuable information for forensic analysis in the event of a security breach. IDS systems monitor network traffic in real-time and alert administrators of any suspicious activity, providing an early warning of potential security threats.
This component involves responding to security incidents and minimizing their impact. This includes incident response planning, incident handling procedures, and crisis management processes. For example, an incident response in an ICS may involve isolating affected systems, conducting investigations, and restoring normal operations. These processes provide a framework for responding to security incidents, ensuring a timely and effective response, and minimizing damage and downtime. A comprehensive security plan that includes these elements helps organizations maintain the security and reliability of their critical infrastructure.
This component involves recovering from a security incident and restoring normal operations. This includes disaster recovery planning, data backup and recovery, and business continuity planning.


Disaster recovery planning helps organizations prepare for and respond to unexpected events, such as natural disasters, cyberattacks, or system failures, that may impact their critical infrastructure. Data backup and recovery strategies ensure that important data is protected and can be restored in the event of a disaster. Business continuity planning focuses on maintaining critical business operations in the event of a disruption, reducing downtime and minimizing the impact on customers and stakeholders. By implementing these strategies, organizations can protect their critical infrastructure against unexpected events and maintain operational continuity.
In conclusion, the NIST Cybersecurity Framework provides a comprehensive approach to managing and reducing cybersecurity risk in OT systems. By following the framework’s guidance, organizations can protect their critical infrastructure and reduce the impact of cyber threats on their operations. However, it’s crucial for organizations to continuously assess their security posture and stay vigilant against evolving cyber threats to ensure the security of their OT systems.

Industrial Cybersecurity
September 28, 2023
Want always be up to date?
By subscribing to our mailing list, you will be enrolled to receive our new trainings, latest blog posts, product news, and more.
Transform your cybersecurity skills with CIP Cyber’s comprehensive training & course offerings

Believe it or not, Industrial Control Systems and Operational Technology (ICS/OT), the lifelines of our critical infrastructure, are seeing rising threats. Last year, more than

The energy sector’s importance is underscored by its designation as an “enabling function” across all critical infrastructure sectors, as per Presidential Policy Directive 21. Serving

The adoption of Industrial Internet of Things (IIoT) devices is rapidly increasing across various industries, bringing significant benefits such as increased efficiency, reduced downtime, and
Want always be up to date?
By subscribing to our mailing list, you will be enrolled to receive our new trainings, latest blog posts, product news, and more.
Transform your cybersecurity skills with CIP Cyber’s comprehensive training & course offerings