
Password Cyberattack: Everything You Need to Know
Cybersecurity leaders consistently rank passwords among the top concerns, recognizing them as critical gateways to sensitive data but also as prime targets for malicious entities.

The manufacturing industry is becoming increasingly vulnerable to cyberattacks, as digital transformation and growing reliance on connected devices expose organizations to new threats. These cyberthreats pose significant risks to operational technology (OT) and critical infrastructure. The rise in ransomware and cyberattacks targeting endpoint devices in the OT environment makes endpoint resilience more important than ever for manufacturing organizations.
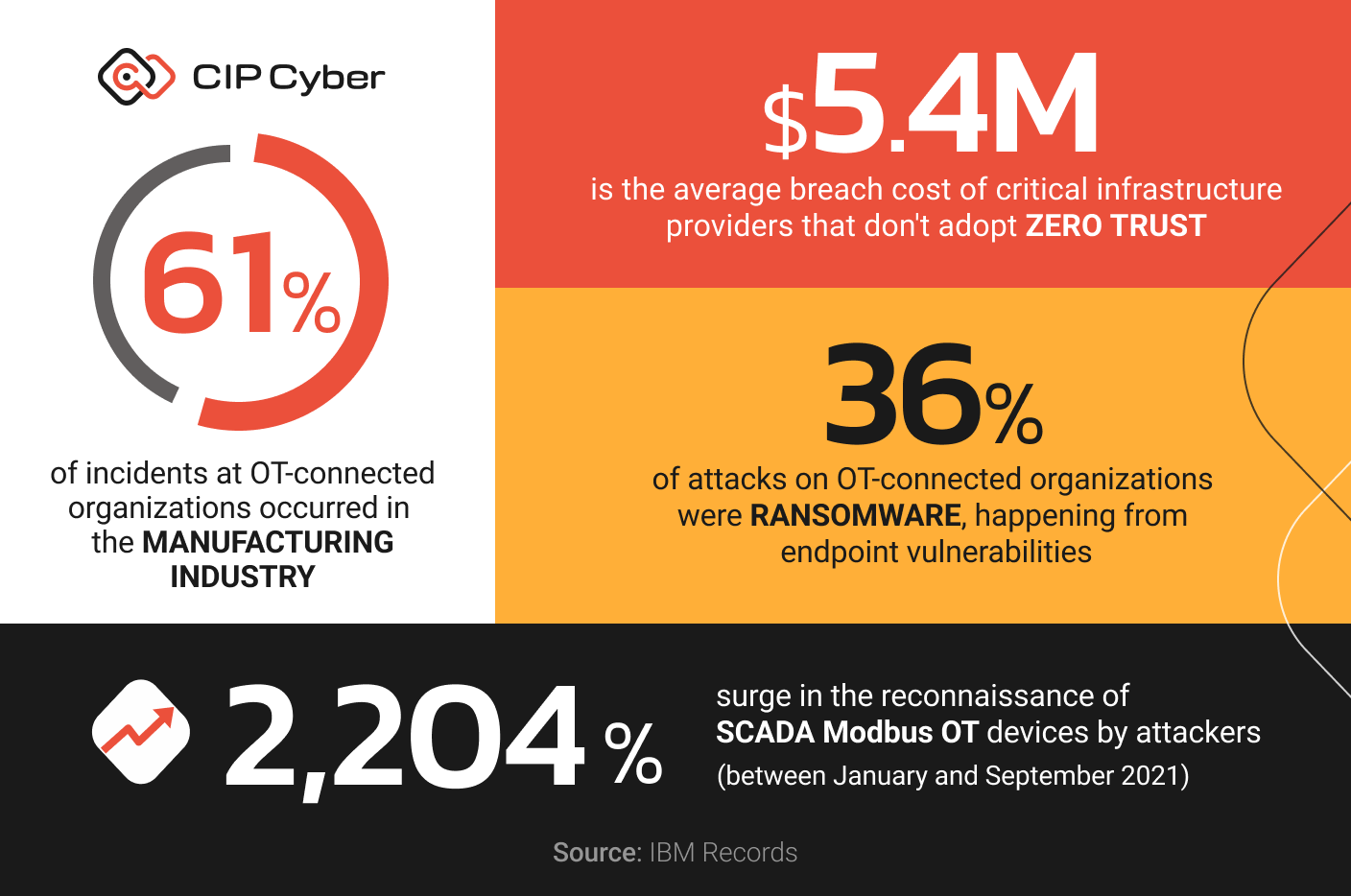
According to IBM Security’s X-Force Threat Intelligence Index, manufacturing was the most targeted sector for ransomware cyberattacks and the most extorted industry in 2022. A staggering 61% of incidents at OT-connected organizations last year occurred in the manufacturing industry. Furthermore, 36% of attacks on OT-connected organizations were ransomware, with many of these attacks exploiting endpoint device vulnerabilities. Attackers increased their reconnaissance of SCADA Modbus OT devices accessible via the internet by 2,204% between January and September 2021, further highlighting the growing threat to endpoint devices.
In addition, recent reports have revealed alarming statistics concerning the state of endpoint security in critical infrastructure organizations. IBM Security found that almost 80% of critical infrastructure organizations studied don’t adopt zero trust strategies, resulting in average breach costs rising to $5.4 million – a $1.17 million increase compared to those that do. Moreover, 28% of breaches amongst these organizations were ransomware or destructive attacks. These statistics underscore the need for a proactive approach to endpoint security in the manufacturing sector, focusing on endpoint resilience and effective security strategies.
To overcome these challenges and protect their critical infrastructure, manufacturing organizations need to adopt a proactive approach that involves monitoring the health of security applications, deploying endpoint detection and response tools, and educating their employees on best practices.
Endpoint management and security present various challenges for critical infrastructure organizations, particularly in the manufacturing sector. These challenges include:
Endpoint resilience is crucial for critical infrastructure security in the manufacturing sector. The concept of endpoint resilience involves the ability of endpoints to withstand cyberattacks and recover quickly from them, minimizing the impact on the organization’s operations and services.
Endpoint resilience can help protect organizations from various threats, such as ransomware, malware, or denial-of-service attacks. It can also help organizations reduce the costs and consequences of a breach. For example, endpoint resilience can enable organizations to remotely detect and respond to incidents, restore corrupted or deleted files or applications, and enforce security policies and compliance standards.
A study by Statista found that the global endpoint security market size is projected to reach US$19 billion in 2025, emphasizing the importance of endpoint resilience.
Torsten George, a cybersecurity expert, said, “When establishing visibility and security controls across endpoints, security professionals need to understand that each endpoint bears some or all responsibility for its own security.” This means that each endpoint device should have encryption, anti-virus, firewall, and application control software installed and updated regularly. This way, even if the network security is compromised, the endpoint device can still prevent or limit the damage caused by an attack.
Manufacturing organizations can implement endpoint resilience strategies by taking the following steps:
Manufacturing organizations face unprecedented challenges in managing and securing their endpoints, which are essential for their operations and services. By adopting a proactive approach that involves monitoring the health of security applications, deploying endpoint detection and response tools, and educating employees on best practices, these organizations can achieve endpoint resilience. This resilience is crucial for the security and reliability of critical infrastructure in the manufacturing sector, as it helps protect organizations’ data, systems, and customers from various threats, reduces the costs and consequences of a breach, and ensures the resilience of their critical infrastructure.

Industrial Cybersecurity
September 28, 2023
Want always be up to date?
By subscribing to our mailing list, you will be enrolled to receive our new trainings, latest blog posts, product news, and more.
Transform your cybersecurity skills with CIP Cyber’s comprehensive training & course offerings

Cybersecurity leaders consistently rank passwords among the top concerns, recognizing them as critical gateways to sensitive data but also as prime targets for malicious entities.

The Internet of Things (IoT) is reshaping our world. As sectors ranging from healthcare to manufacturing integrate IoT technology into their operations, we can expect

Even as the digital revolution continues to reshape industries, a significant portion of the ICS/OT sector remains vulnerable to cyberattacks, with email phishing as a
Want always be up to date?
By subscribing to our mailing list, you will be enrolled to receive our new trainings, latest blog posts, product news, and more.
Transform your cybersecurity skills with CIP Cyber’s comprehensive training & course offerings